AWS Lambda is a serverless, event-driven computing service that allows you to easily run code. AWS will manage the entire environment, allowing organizations to concentrate on the application itself.
The main benefits of Lambda are:
- No resource provisioning or server management is required to automatically run function code.
- Scaling serverless applications automatically by running code in response to event triggers. Serverless code executes in parallel, with each process triggering on its own, scaling to the workload's exact size.
- Billing is based on the number of times the code is triggered and the number of 100 milliseconds it executes.
The serverless approach allows the development process to focus solely on the core product rather than the time-consuming task of constantly applying security patches to the underlying operating system and application servers - these tasks are now the responsibility of the serverless architecture provider.
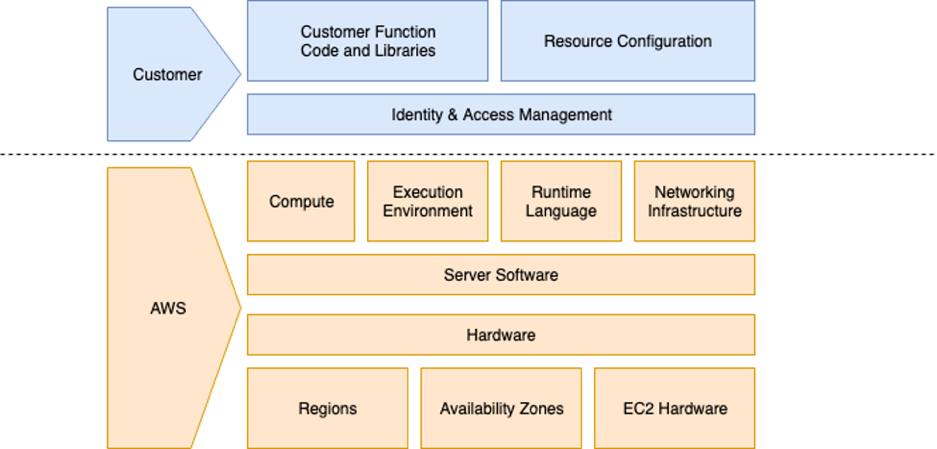
Lambda Shared Responsibility Model
However, there are still security safeguards in place for all application logic, code, data, and configuration, for which the application owner is responsible.
Here are some Lambda security best practices you can use to keep your function safe:
Using Least privilege IAM Role
The Identity and Access Management (IAM) role is an Amazon Web Services (AWS) service that is used to assign permission policies to each entity. The management of IAM roles may be tedious and time-consuming, but each function should have its own IAM role, and each role should have only the bare minimum of access to other services. Even if one of the functions is vulnerable and abused, this reduces the impact on the resource.
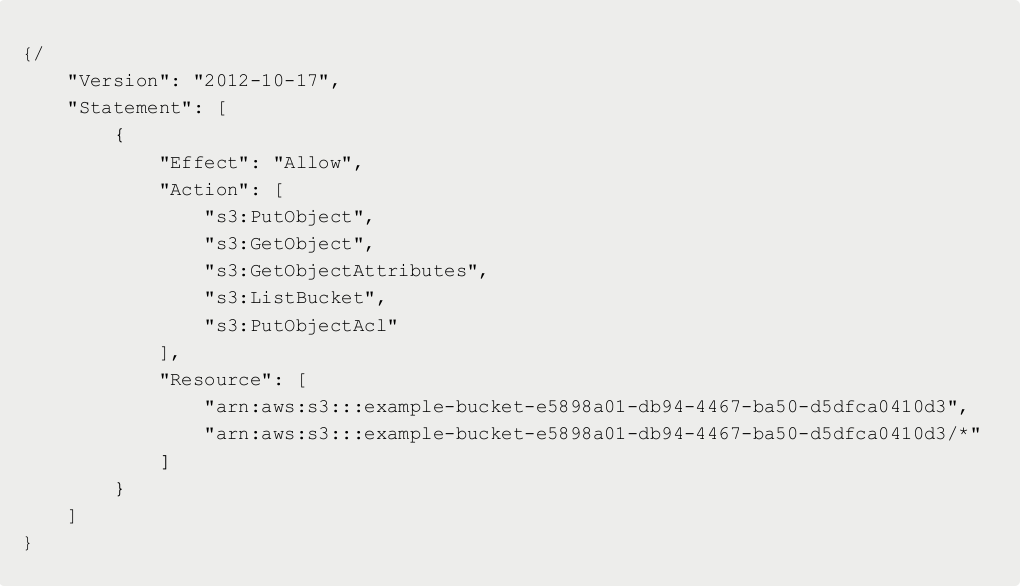
For example, a Lambda function that needs Read & Writes access to the bucket should get an IAM role that has access to only that bucket with minimum permissions. So the IAM for that Lambda should be:
Protecting your secrets
There are many keys and password you need to hide from the actual code and AWS offer some method to protect it
- Using Environment variable with Encryption helpers
- Using other AWS services like AWS Systems Manager Parameter Store or AWS Secrets Manager
For small independent functions, using environment variables may suffice; however, managing several functions in a large service can be difficult. Each function requires access to the same resource, such as database authentication, thus you should use a service like AWS Secrets Manager to keep track of all the secrets that must be shared across functions.
Using API gateway to access Lambda
There are several ways to access and run your Lambda function, such as calling directly from the CLI or using the SDK, but the most common is to use an API Gateway. API gateways offer numerous advantages, including load balancing, monitoring, and API versioning. However, when using API Gateway, the ability to secure your Lambda via VPC is lost, necessitating the use of alternative methods to protect your API. API Gateway provides some options for accomplishing this:
API keys:
API Gateway provides API keys and usage plans to allow you to control who has access to your APIs. This can be used to set the target rate for throttling requests and protect your API. However, this should not be your only method of API security because an API key for one API can be used to access all APIs in the usage plan; instead, use it in conjunction with an Authorizer to provide role-based access control to your API.
Authorizers
- Cognito: Cognito is a good way to control who can access your API in an API Gateway. With a user pool, you can sign in to your app using Cognito as well as other identity providers such as Google, Facebook, or Apple, as well as SAML identity providers.
- Lambda Authorizer: As the name implies, a Lambda Authorizer is an authentication method that uses a Lambda function to generate an IAM policy based on client identity. A Lambda authorizer is useful if you want to implement a custom authorization scheme that uses a bearer token authentication strategy, such as OAuth or SAML, or that uses request parameters to determine the caller's identity.
- Mixed: You can also combine them, with Cognito providing the token and Lambda
Authorizer consuming it. More information can be found here.
Secure your Code
Check for vulnerable dependencies: It is important to note that when importing code from a vulnerable third-party dependency, even the most secure serverless function can become vulnerable.
Check for input: In many cases, AWS Lambda functions consume event input from various event sources, and this input may include a variety of message formats and encoding schemes depending on the type of event and its source. These messages' various data elements may contain attacker-controlled or otherwise dangerous inputs. Keeping this in mind, you should verify all of the input that Lambda consumes using schema and logic. For example, in Python, utilizing the schema library to check for input for not only type or encoding, but also regex, multiple logic like and, or is a good choice.
Monitor your code executions: Because billing is based on the number of times the code is triggered and the amount of time it executes, you must monitor the executions of AWS Lambda functions to find out if there are any problems or if an attack is occurring to your function. Some of the metrics you should monitor are throttling metrics, and errors metrics, specifically for timeouts. It is strongly advised that you set up monitoring and alerts for your AWS charges and billing. Monitoring errors in Lambda is difficult since they might be caused by several resources at the same time. To overcome this problem, instead of only utilizing CloudWatch, you can use Lambda Insight to troubleshoot issues with your Lambda functions. To enable Lambda Insight for your function, follow the steps from this page.
About FPT Software
FPT Software is a global technology and IT services provider headquartered in Vietnam, with more than USD 600 million in revenue and 22,000 employees in 26 countries. As a pioneer in digital transformation, the company delivers world-class services in the Smart factory, Digital platforms, RPA, AI, IoT, Cloud, AR/VR, BPO, and more. It has served 1000+ customers worldwide, a hundred of which are Fortune Global 500 companies in the industries of Automotive, Banking and Finance, Logistics & Transportation, Utilities, and more. For more information, please visit https://www.fpt-software.com.