Do you still confuse about Blockchain security? This article will give you the overview of Blockchain security through 4 examples.
The basic concept
Before moving on to the main section, where we deep dive into how the blockchain security works under the hood. Let’s have a look at some basic features of blockchain to have a general understanding of it.
According to Imran Bashir (2017):
Blockchain at its core is a peer-to-peer distributed ledger that is cryptographically secure, append only, immutable and updatable only via consensus or agreement among peers (p. 54).
That sounds quite confusing, right? However, blockchain is much easier than that definition. Blockchain – as the name suggests, it is simply a chain of blocks and each block references the previous one by the unique “block's hash”. The term “block” here is simply a database which stores digital information about the so-called “transaction”. Once the data was stored in blockchain, it is immutable. You can only append a new block to the chain and put the new data into it.
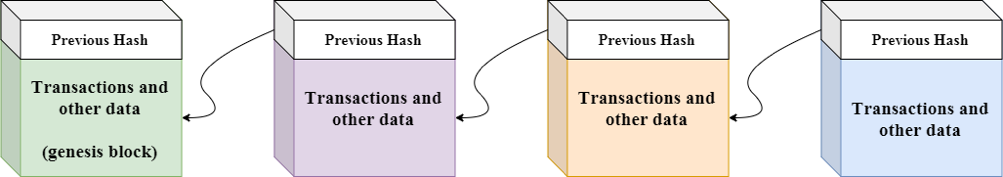
Besides, the blockchain network is a decentralized and distributed system, it has no central authority but instead, it is shared and open for everyone to see. Therefore, everything built on blockchain is very transparent, trusted and users take full of responsibility for their actions.
(Related: Blockchain Monitoring Portal: Secret Weapon in Blockchain Projects)
#Problem 1: What would happen if you changed the data inside a block?
#Example 1:
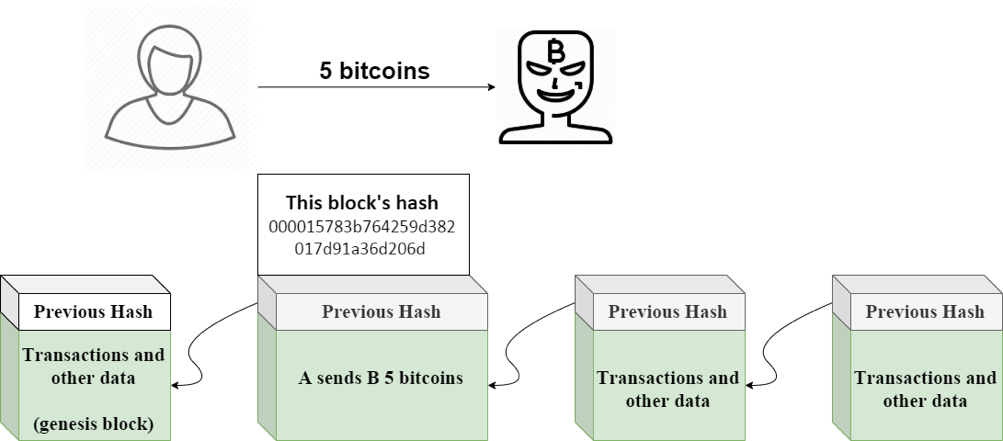
A transferred B an amount of 5 bitcoins, and this transaction was stored inside the #2 block with the hash of 000015783b764259d382017d91a36d206d and this block is considered valid since it has 4 zeros at beginning. However, B is a scammer and he wants to go back in time, change the transaction’s information and tell that A sent him a value of 10 bitcoins.
In fact, it’s not that easy for anyone in the world to do so. Whenever you alter the data inside a block, that block will automatically recalculate the hash and become invalid. Hence, all the remaining blocks after the modified one are then invalid too.
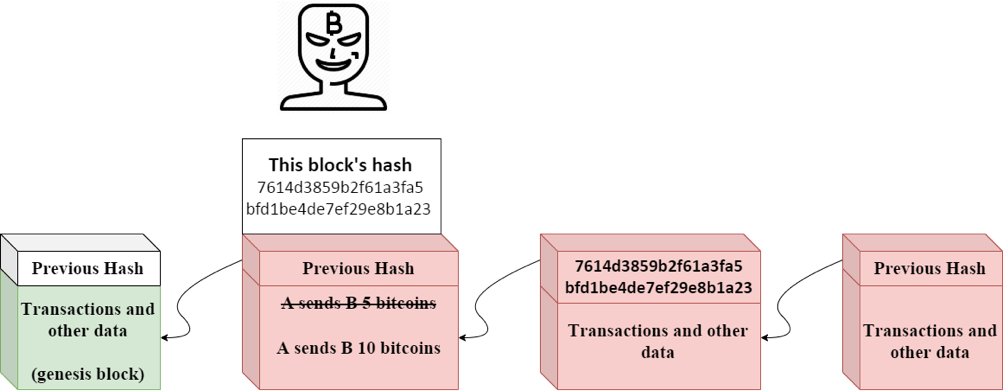
Back to the story, when B does some changes to the data inside the #2 block, the hash will then turn into, for example, 7614d3859b2f61a3fa5bfd1be4de7ef29e8b1a23. And this block is now considered invalid since its hash no longer starts with 4 zeros anymore.
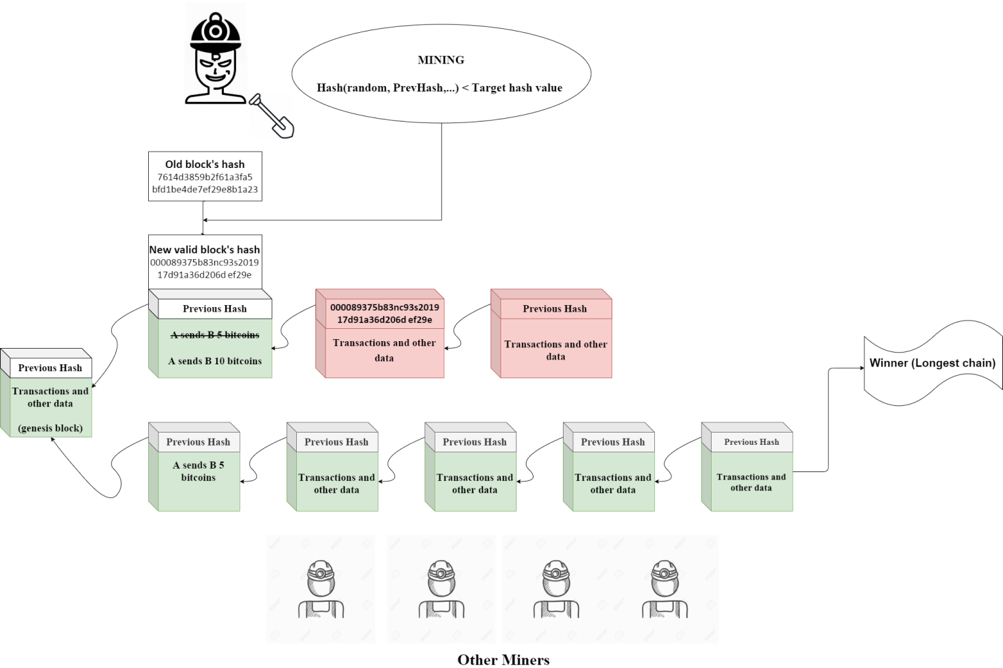
To make it valid again, B has to solve a mathematical problem to find a random number so that the resultant hash is lower than a target hash value and this process is called “mining”. However, not only does B have to solve the modified block’s mathematical problem, but all the remaining blocks’ after that one as well. In other words, B now is building his own new chain of blocks.
Additionally, because of the “Proof of work” consensus algorithm used in Bitcoin and other cryptocurrencies, the process of mining requires a lot of computational resources and can take about 10 minutes to find a valid hash in the Bitcoin network. Furthermore, the network, in the end, will naturally switch to the longest chain. In this case, the smaller chains will be considered orphaned. It means that B is now competing against the world to build his own chain and the chance of B winning this race is even lower than that of winning a lottery. Only when B owns 51% control of the network’s hash rate (computational power), then he can, of course, reverse any transactions appeared in the blockchain he likes.
(Related: Smart Factories of the Post-Pandemic Future)
Transaction and verification process:
Transaction is the fundamental unit of blockchain. A transaction represents a transfer of value between two different people. In the blockchain world, once a transaction is propagated, it is then validated based on a predetermined set of rules by the other peers on the network and only valid transactions are selected for inclusion in a block.
#Problem 2: Considering the case that someone tries to kind of forge your own identity to send your money to his/her account. How do the others know whether you are exactly the one who submits that transaction or not?
In fact, each user has a private-public key pair. A private key - as the name suggests, it is kept secret and held privately by the users while a public key is the public part of the private-public key pair, it is available publicly and published by the private key owner.
#Example 2:
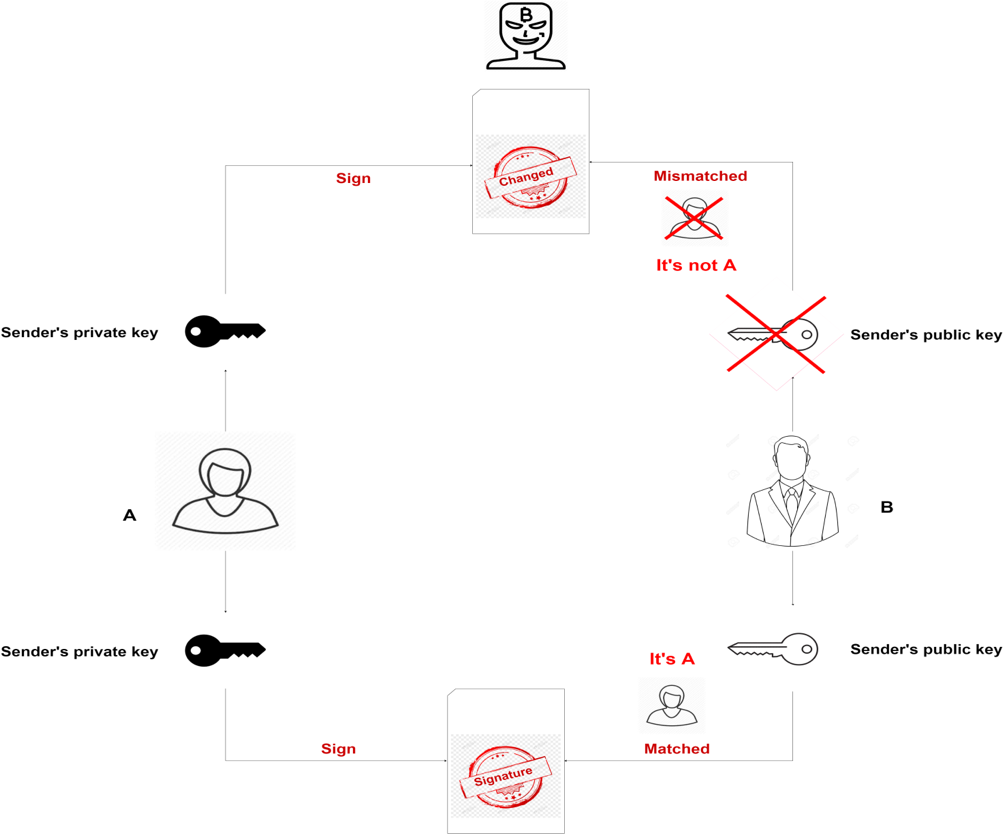
When a sender sends a transaction, he signs the transaction using his private key and generates a corresponding public key. The sender, then, transmits the transaction over the network to the recipient. Once the recipient receives the transaction, it will be verified for its integrity by the sender’s public key. Any attempt to tamper with the information in the transaction while it is broadcast is pointless because the sender’s public key will then be mismatched and the transaction will be rejected due to its invalidity. No one can fake your identity unless he/she somehow knows your private key.
#Problem 3: How does blockchain - a decentralized and distributed ledger keeps track of users’ balance. How do we verify whether someone does indeed has 5 bitcoins when he sends that amount of bitcoins to someone else?
In actuality, blockchain does not work that way, it does not know how many bitcoins you have at all, it is simply used for storing transactions.
In Bitcoin, each transaction contains metadata, inputs and outputs. Generally, each input spends an output from the prior transaction and generate a new output that can be spent as an input to a new transaction in the future. Each output has two fields; the first field is the amount of Satoshis (the smallest unit of Bitcoin) whereas the second field is a locking script (think of it like a real lock and only the owner who has the key can unlock it and spend that amount of Satoshis). Each output is considered an Unspent Transaction Output (UTXO) until an input consumes it and all the UTXOs are used to calculate the total amount of bitcoins – the balance of your wallet. Let’s take a look at a simplified example to see how UTXOs work in Bitcoin transactions.
#Example 3:
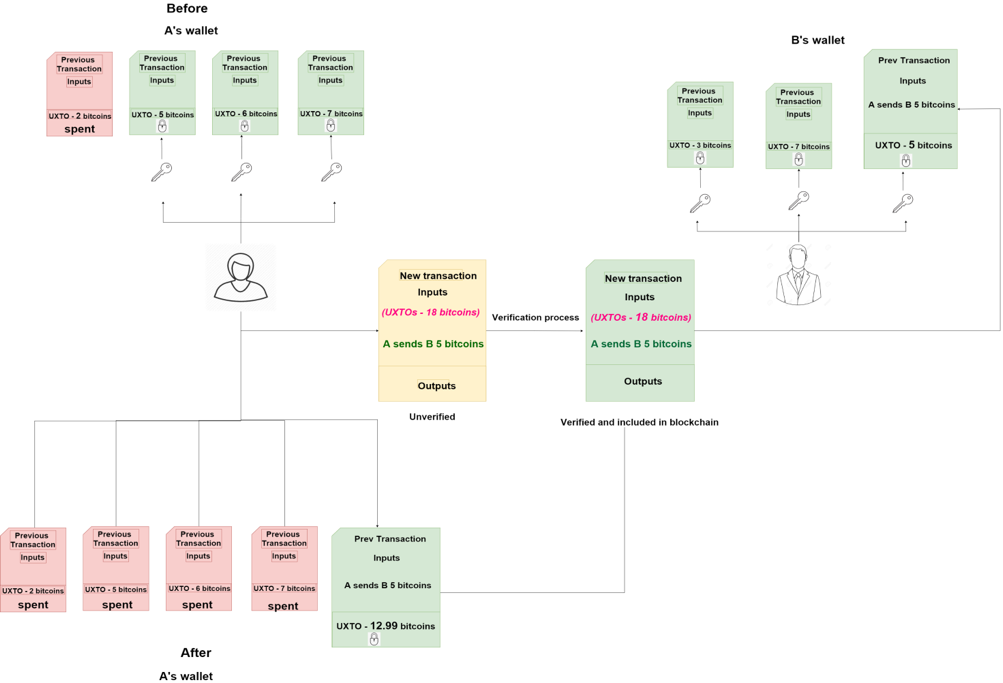
- At present, A has 3 UTXOs recording of totally 18 bitcoins as rewards for mining new blocks.
- A wants to send B 5 bitcoins for a new laptop, so she has to make a new transaction, right?
- First, A unlocks 3 UTXOs in her previous transactions.
- Secondly, A takes the whole 3 UTXOs she has as 3 inputs to the new transaction and sends it to the network.
- Finally, after being verified and added to blockchain, the transaction adds 5 bitcoins to B’s wallet and the remainder of 12.99 bitcoins (due to the transaction fee of 0.01 bitcoins) is sent back to A in the form of a new UTXO. Three previous UTXOs are considered to be spent and cannot be used anymore.
(You might also like reading: Privacy In A Data-Driven Society)
#Problem 4: The procedure above has one significant weakness. What would happen if A sent 2 transactions simultaneously, one to herself and another to B. This is called as double-spending attack. Let’s figure it out in the last example in this article.
#Example 4:
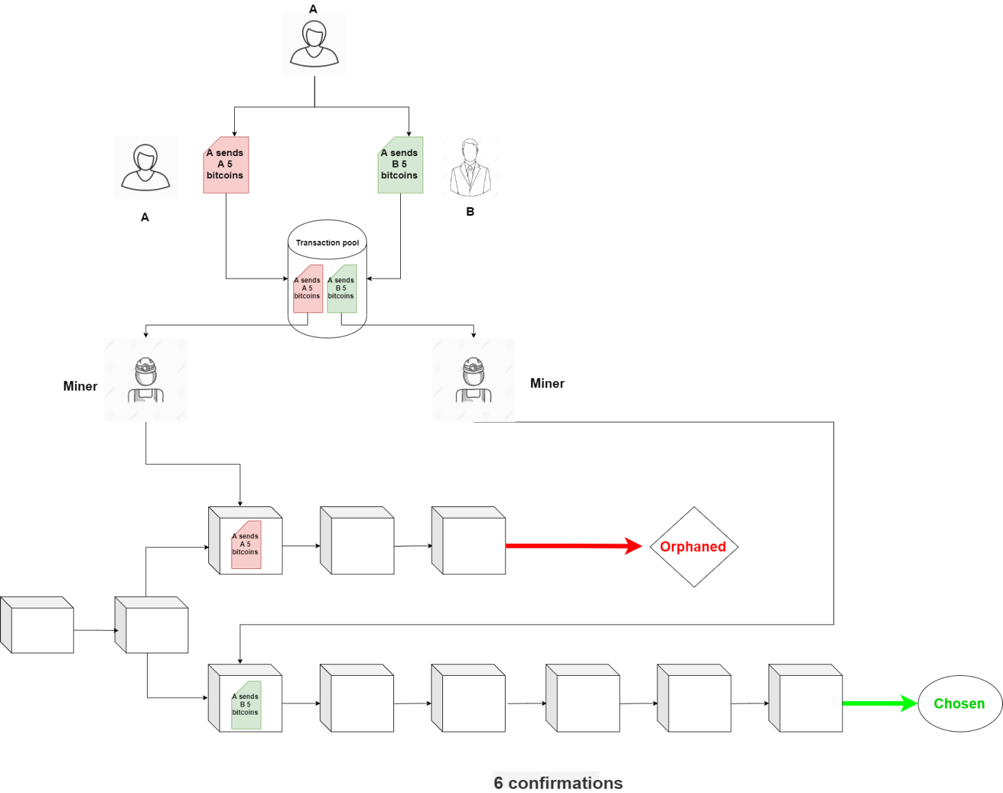
Assumed that A is a swindler, at the same time she sends B 5 bitcoins and also sends herself that amount of bitcoins. Both transactions, of course, spend the same 3 UTXOs in the previous transactions, right? They are then sent to the transaction pool (a place to store all unconfirmed transactions) and from where the miners pick up transactions based on their priority to include them in a new block. However, because they are sent at the same time, there will be two scenarios:
- Case 1: If one of those two transactions is picked up and included in a new block before the other, the 3 UTXOs are then considered to be spent. So the other transaction spending the same 3 those UTXOs will become invalid and be rejected. However, in this case, B will immediately realize that A has cheated him.
- Case 2: Both transactions are picked up simultaneously by two different miners and included in two different blocks at the same time. Back to #Example 1, there can be multiple chains, but the network chooses only the longest chain. So in the end, there’s still only one transaction included in the blockchain and the other is rejected. But this time, B cannot be immediately aware of the outcome. To avoid the chance of being cheated by A, B should wait for the longest chain to be chosen.
It is recommended that you should wait for a minimum of 6 confirmations. Here, “6 confirmations” simply means that after a transaction was added to the blockchain, 6 more blocks containing several other transactions were added after it. The key idea behind waiting for six confirmations is that the probability of double spending is virtually eliminated after six confirmations.
For more readings on technology, click here to explore!
Reference
[1] Imran Bashir (2017). Mastering Blockchain. Birmingham, UK: Packt Publishing Ltd.
[2] Anders Brownworth, Blockchain Demo. Accessed October 13, 2019. Retrieved from: https://anders.com/blockchain/ .
[3] Lin, I., & Liao, T. (2017). A Survey of Blockchain Security Issues and Challenges. I. J. Network Security, 19, 653-659.